Hello. Welcome to my blog. I will take you through the Deep Blue challenge found at https://blueteamlabs.online/home/investigation/deep-blue-a4c18ce507 (username is: btlo and no password)
The given scenario is: ‘A Windows workstation was recently compromised, and evidence suggests it was an attack against internet-facing RDP, then Meterpreter was deployed to conduct ‘Actions on Objectives’. Can you verify these findings?’
To work through this, we will use the DeepBlueCLI - a powershell module for Threat Hunting in Windows event log - and Windows event viewer - a builtin tool in the Windows OS for viewing and analyzing event logs.
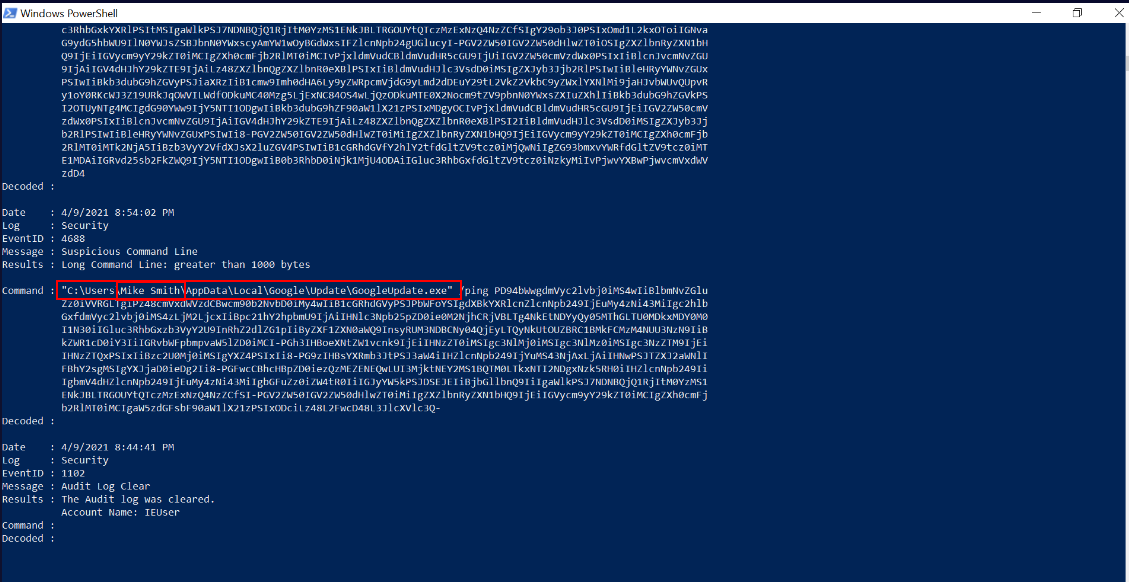
Q1 Using DeepBlueCLI, investigate the recovered Security log (Security.evtx). Which user account ran GoogleUpdate.exe? (4 points)
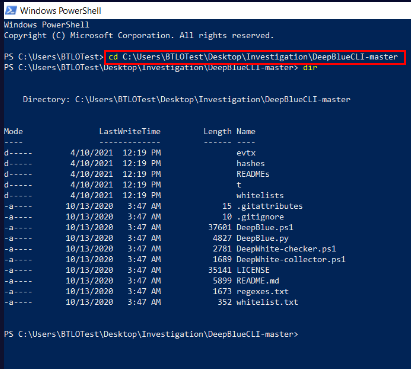
Here, the first step is to launch Windows Powershell and navigate into the directory containing the resources
The syntax for opening the log file in DeepBlueCLI is:
1
.\DeepBlue.ps1 .\evtx\security.evtx
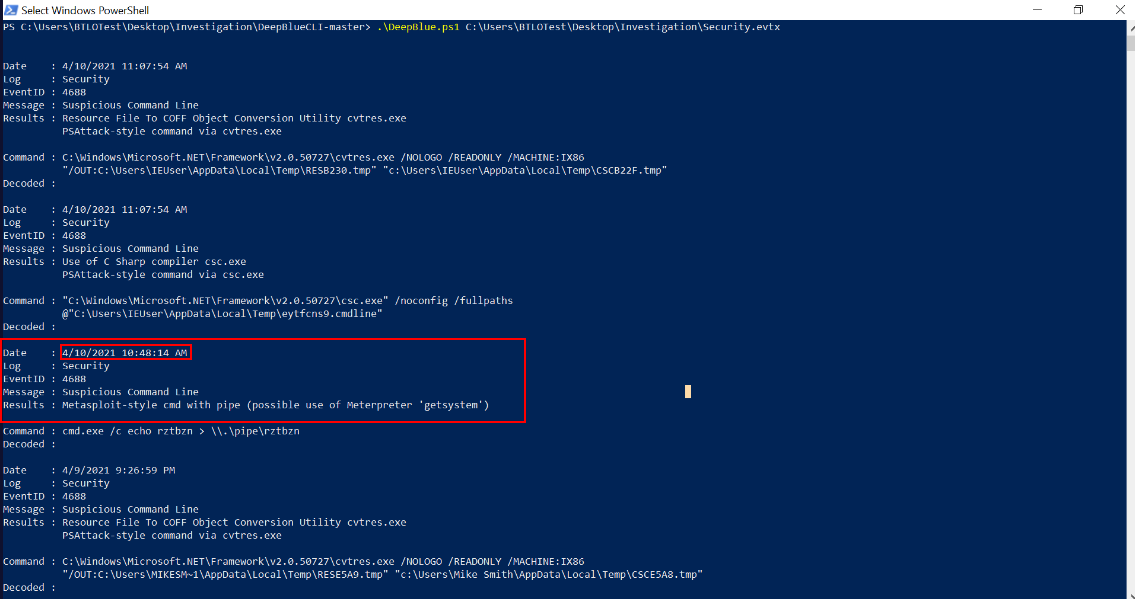
Q2 Using DeepBlueCLI investigate the recovered Security.evtx log. At what time is there likely evidence of Meterpreter activity? (4 points)
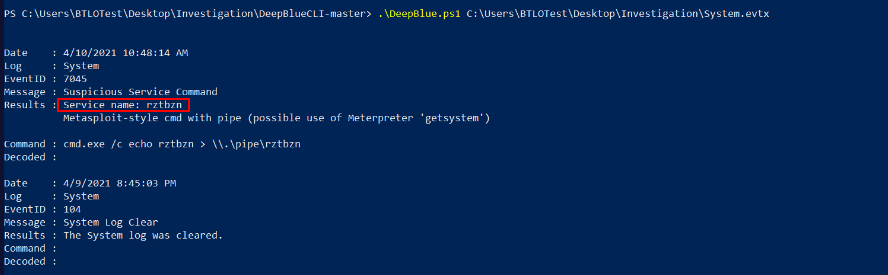
Q3 Using DeepBlueCLI investigate the recovered System.evtx log. What is the name of the suspicious service created? (5 points)
Q4 Investigate the Security.evtx log in Event Viewer. Process creation is being audited (event ID 4688). Identify the malicious executable downloaded that was used to gain a Meterpreter reverse shell, between 10:30 and 10:50 AM on the 10th of April 2021. (4 points)
Here, we now use the Event Viewer to analyze the Security.evtx log. Luckily, from the second question above, we know the event timelines which makes it easier to brush through the logs.
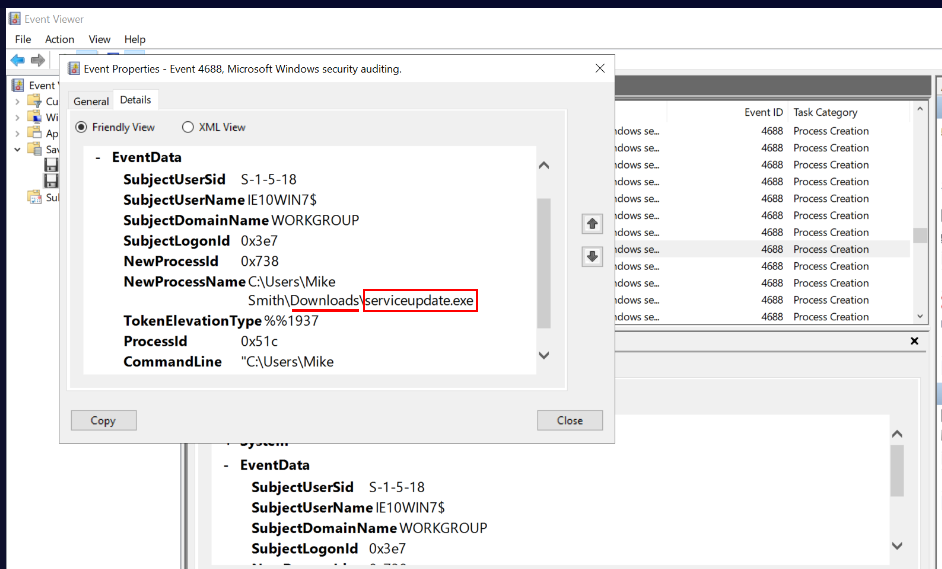 Answer: Mike Smith, serviceupdate.exe
Answer: Mike Smith, serviceupdate.exe
Q5 It’s also believed that an additional account was created to ensure persistence between 11:25 AM and 11:40 AM on the 10th April 2021. What was the command line used to create this account? (Make sure you’ve found the right account!) (4 points)
Here, we are looking for an account creation event. One approach would be to search using the keyword ‘add’ or to explore manually. I choose to go the manual way since it helps correlate between the events occurrence
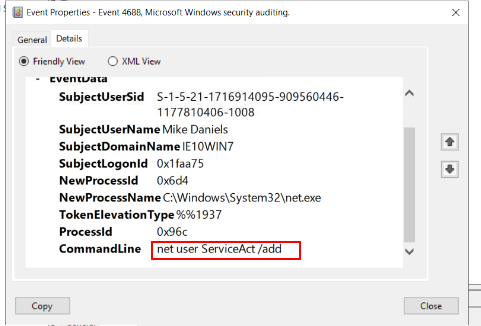 Answer: net user ServiceAct /add
Answer: net user ServiceAct /add
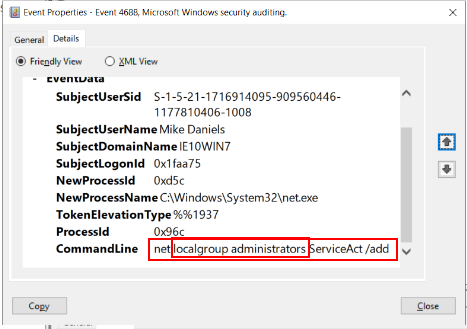
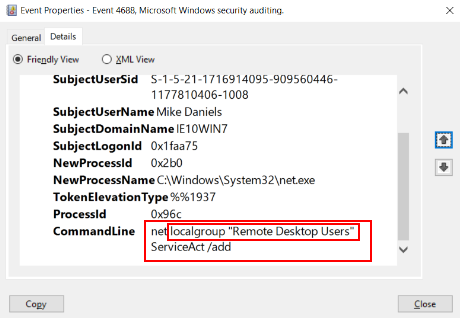
Q6 What two local groups was this new account added to? (4 points)
From the above account creation event, it is obvious that adding the account to privileged local groups follows. This was captured in the logs
For additional reading resources:
https://github.com/sans-blue-team/DeepBlueCLI